Enhanced Access Control Precision
CoSec Global's role-based authentication empowers meticulous control over who can access specific resources or undertake particular actions within a system.

Scalability
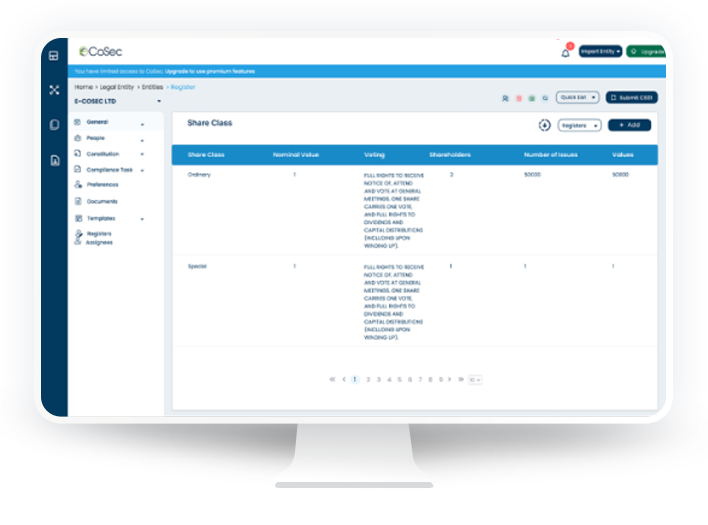
Our role-based authentication solution scales effectively by facilitating the assignment of new users to existing roles and accommodating the incorporation of fresh roles to adapt to evolving organizational structures.
Adaptability and Versatility
Our role-based authentication system can be tailored to various situations and applications, tailored to the specific requirements of the environment.

Efficient Maintenance
In cases where permissions or access prerequisites require modifications, administrators can modify roles instead of individually adjusting permissions for each user, simplifying maintenance efforts.